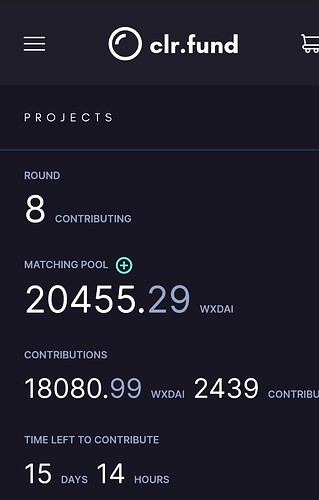
With a little over two weeks to go in round 8, we’re already more than 4x our previous all-time high in number of contributors.
This is good! 
But is it a little too good?.. 
Do we have a Sybil problem this round?
I have a suspicion that some of this round’s volume is users attempting to farm airdrops. That being the case, it’s logical that some users would attempt to create multiple accounts.
To be clear, there is no CLRFund airdrop and CLRFund’s design makes it impossible for recipient projects to know who their contributors are and reward them with airdrops. So CLRFund will be a fruitless airdrop farm.
What are the best tools we could use to assess and identify patterns of Sybils and collision in the round?
I see three potential layers that could be analyzed.
- Ethereum address: contributions to the round are public, even though allocations within the round are secret, so we could map the relationships between all of the addresses that contributed to the round to see if there are any patterns that indicate collusion.
- BrightID node: the BrightID node has data linking Ethereum address to BrightID identifier, meaning that it can (and already does) analyze the relationships between these accounts. It could be useful for us to map the connections between accounts that participated in the round.
- Coordinator: the coordinator has privileged access to encrypted vote data. They could map the allocation patterns of contributors. We should only do this if it is possible to do without revealing additional information that could enable collusion.
Does anyone have suggestions on who might be the right person to tackle 1?
2 and 3 will necessarily need to be performed by the BrightID node operators and CLRFund’s coordinator, respectively, and 3 should probably only happen as a last resort if 1 and/or 2 indicate something fishy.